Iroquois’ In-House Counsel Janine Fodor joins us to talk about the importance of knowing where your data is and that it is properly protected. This is an overview of the current landscape in data privacy and cyber security law. Janine reveals that what was once considered optional best practices are now concrete laws. She outlines how an agency can get into trouble. As well as helps us better understand why we might want that cyber liability policy to protect ourselves. Finally, Janine gives us some great tips on how we can start the journey to a safer cyber environment. For more on cyber security check in here.
Edwin K. Morris (4s):
Welcome to the trusted advisor podcast brought to you by Iroquois group. Iroquois is your trusted advisor in all things insurance. I am Edwin K. Morris. Today’s guest is Janine Fodor. She is the in-house counsel for the Iroquois group and has been working in that role since 2013. Before that, Janine was a partner in the law firm of Wagner and heart, where she performed insurance defense and other kinds of business litigation. Please note that this podcast is for general informational purposes only. It is not intended to be legal advice and should not be relied upon as legal advice.
Edwin K. Morris (45s):
Can you describe for me, or give me a detail of what cybersecurity even means?
Janine Fodor (49s):
Cybersecurity involves taking steps to protect the data that you collect or send, primarily by making sure that the electronic systems that you use, your computers and your servers and any data storage device that you have, can’t be hacked and the systems don’t leak, that is people don’t negligently end up disseminating data that should be confidential and protected.
Edwin K. Morris (1m 17s):
What now is applicable for agencies to be concerned with that are one, a liability and two, is there a law or any kind of construct around what has to be done?
Janine Fodor (1m 29s):
Well, the law is, I would say quickly evolving. So most of the law that exists now is at the state level, but more and more States are beginning to adopt regulations that require insurance agencies to have certain protections in place. For example, to limit the access to their systems to authorized users, a matter of good pract- of good business practice, but increasingly it’s a matter of regulation and law. And all States currently require any business whose customer data is leaked that is that the customer data is either stolen, might be in the hands of somebody who shouldn’t have it, They have to notify all those customers.
Janine Fodor (2m 15s):
It’s called a breach notification law. All States have that for that reason alone, just to prevent yourself from having to be in the situation where you’re required to notify all of your customers that their data might’ve been taken. That’s reason enough to take proactive steps to protect your systems against a breach.
Edwin K. Morris (2m 34s):
That’s if you know that that happens, right? That’s a big if, right? I mean, to be aware of that breach happening is one thing. But
Janine Fodor (2m 43s):
Although I think that people do see signs of their data having been compromised or breached, for example, increasingly the bad guys are using what’s called ransomware, meaning that you will actually get a message on your computer that somebody has your data and they will demand a payment in exchange for returning that data to you. Obviously, people who have taken your data are not very trustworthy. And many people have reported that even if they pay the ransom and try to get their data back, that the data comes back essentially unusable or has been compromised or destroyed in ways that recovering it is a huge problem.
Janine Fodor (3m 25s):
So not only have the bad guys got a copy of your data, but in fact, you may never get your data back in, in the form that it was before it was taken for ransom.
Edwin K. Morris (3m 37s):
And that becomes a sellable product on the criminal side.
Janine Fodor (3m 39s):
Absolutely. And we’re talking for insurance agencies, just think about the value of the data that they collect from consumers. They might have driver’s license numbers, addresses, a lot of data that would be of a huge amount of value if it was disseminated throughout the web. And, and so I think it’s particularly incumbent upon people in the insurance industry to be aware of the risks.
Edwin K. Morris (4m 2s):
How much of a heavy lift is this for small business to get behind
Janine Fodor (4m 7s):
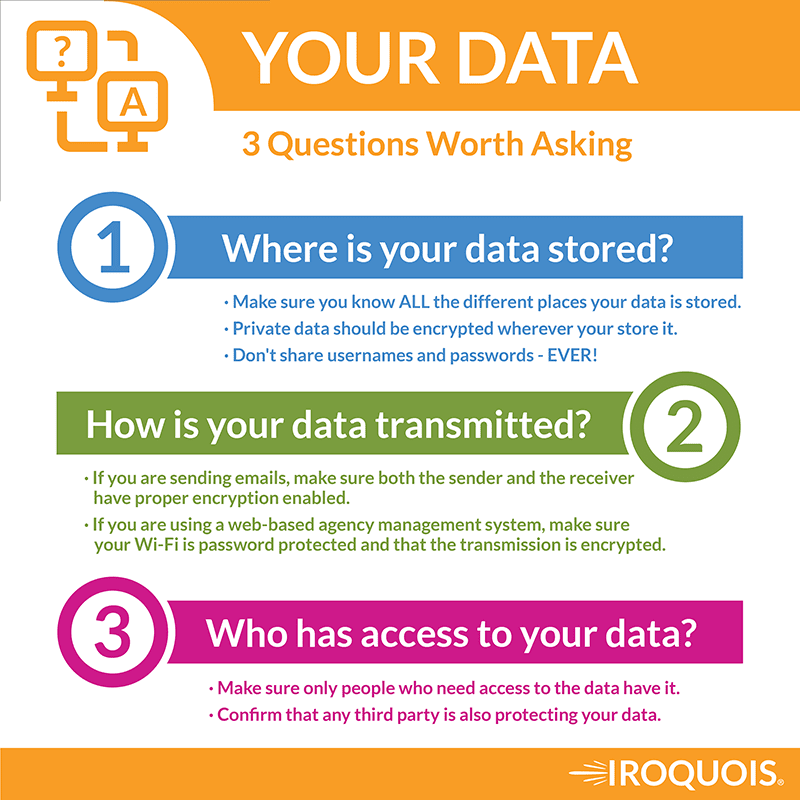
There’s no question that it’s a heavy lift. Most people of my generation were just so unaware of how to begin to take those steps. It’s a daunting task. So because it’s something that we’re just unfamiliar with and, and a little nervous about, we tend to kind of take the ostrich approach and pretend that it’s not going on. The first step would be to talk to an IT professional and have someone do what’s called a risk assessment or a vulnerability assessment of your system. I think the very first, most basic question to ask is where is your data? How are you keeping it?
Janine Fodor (4m 46s):
Is it located on a server in your office? Is it located on, on hard drives or portable devices? Are you accessing your data only through your agency management system and carrier portals, which are likely to be better protected? So I think the very first step is to do sort of an audit. How does data come into your office? Where do you keep it? And then how do you send it out and once
Edwin K. Morris (5m 12s):
And who touches it, right. Who touches it, who has access?
Janine Fodor (5m 15s):
Absolutely. And, and that, and another very basic step that I think every insurance agent should be taking is to make sure that everyone who goes into your systems, goes in with password protected access, that you don’t share those passwords, that you can identify the particular individual who went into a certain database. And that as soon as an employee leaves, you cut off their access to your systems. Right?
Edwin K. Morris (5m 42s):
Well, and we’re probably getting to the point where biometrics will be the next phase, where everybody at a local office would just have a fingerprint reader or eye scanner or something that is a, is a biometric specific where you is.
Janine Fodor (5m 52s):
Yes, I completely agree. I think that we’re, we’re moving in that direction, but today or tomorrow, you know, every retail insurance agency out there can utilize strong passwords and two passwords, sometimes one to get into your computer system. And then a second one to get into wherever the data is securely stored
Edwin K. Morris (6m 15s):
Is there any kind of guidance out there that help get that foundation started?
Janine Fodor (6m 20s):
I think there are two places that agencies can look. One is their agency association. They’ll often have a fair amount of information now on how to start a sort of a cybersecurity program. There is also a, a set of standards that the federal government has generated that are voluntary at this point, they’re not a matter of regulation or law, but they do set forth how you can secure your data. And, and those standards are actually sophisticated. It may take communicating with an IT professional to fully understand how to implement those standards in a small business setting, but they’re out there.
Janine Fodor (7m 4s):
And I think looking at them in communication with an IT professional would help you to understand how to do a reasonable risk assessment of your own business. But the Big I and agency associations have been very aware of this issue. And you typically will have helpful resources. The department of financial services or insurance in your state might also have resources.
Edwin K. Morris (7m 26s):
That’s a helpful to know. So every state has different levels of capacity in that realm.
Janine Fodor (7m 31s):
New York has adopted particular regulations governing the insurance industry. So they, have the department of financial services from New York does have cybersecurity resources on its website.
Edwin K. Morris (7m 44s):
So for someone that’s in a small business that says, you know, I don’t have anything in the cloud. It’s just me, all I’ve got is this laptop and an old PC, what do they need to be concerned with?
Janine Fodor (7m 58s):
Yeah, the state law in this area varies significantly. But I think in my opinion, in the next two to three years, we are going to see a lot more States adopt specific cybersecurity protocols for the insurance industry, kind of following New York’s lead. We also have California, which has moved in a slightly different direction. They’ve got the California consumer privacy act, which governs all businesses and mostly large businesses. And it’s more geared at consumer protection. That is, it requires all companies to inform consumers about where their data is and how they’re using it. And it requires companies to allow consumers to opt out of data sharing in various ways, that there’s a carve out for insurance data under the California consumer privacy act.
Janine Fodor (8m 52s):
So I don’t know how many States you’re going to follow in that, but I think we are going to see possibly federal law, but certainly a lot more state law, which just sets up requirements.
Edwin K. Morris (9m 5s):
Well, and then, you know, things like how access is gained, right. To go to that internet availability. So if you’re on an open system, like in an airport or something like that, or on an airplane, these are not secure internet themselves. So being mindful of where you access and how you access is probably as important as having a pulse.
Janine Fodor (9m 29s):
Yeah, no, that, that’s certainly true. And another thing that I, I would recommend to small businesses, particularly in the insurance industry is to look into getting some amount of cyber liability coverage. So that means buying an insurance policy that would cover those costs if in fact you do have an incident.
Edwin K. Morris (9m 51s):
How long has this been in play? How long has cyber liability been thing?
Janine Fodor (9m 58s):
Well, cyber liability coverage as a possible form of insurance? Well, probably several years, but I think my guess is not that many really small businesses have bought it, have purchased it, but that’s okay.
Edwin K. Morris (10m 12s):
You gotta be a little more likely than earthquake insurance, right? It’s gotta be a little more likely than flood insurance, right?
Janine Fodor (10m 18s):
Absolutely. Yeah. I think it’s got to become a norm. Almost every professional insurance agency will buy errors and omissions insurance, which is professional liability insurance. And I think that cyber liability coverages should and likely will become as common as buying professional liability insurance. Because one of the things, one of the advantages of buying coverage is that you’re also buying some professional help. That is, they will give you some guidance both before you purchase the coverage about what you need in order to qualify for coverage. And then if you do have an incident or you do have a breach, they’ll usually have some forensic resources will, which will help you determine what data got taken and how they got in.
Janine Fodor (11m 4s):
Will also provide you with a resource to do sort of damage mitigation and, and prevention. So
Edwin K. Morris (11m 11s):
I got to ask, is the cybersecurity exactly the same bucket as identity theft?
Janine Fodor (11m 16s):
Yeah… Well, identity theft is one of the risks that occurs when data is taken. But for example, those ransom demands, that’s a separate risk. So, and of course both happen. You could receive a ransom demand and then you don’t really know whether or not the data that has been taken, which they promise to give back, but who knows, that that data might be end up on the internet with people who could then engage in identity theft of the consumers or insureds, who are your customers, right.
Edwin K. Morris (11m 50s):
I wanted to bring that point up is that, you know, for those ostriches that still have their head in the sand, you have to think about the second order effects of the first issue, the theft of the data, the use of the data and all those things that can go for years down the road affecting people.
Janine Fodor (12m 8s):
Yeah, absolutely. And, and I also think a third risk is that once that data is out there, a lot of industries, you know, for example, like recruiters will be building that data that they can scrape from anywhere they can into algorithms that will then affect people’s credit history, their eligibility maybe for health insurance. Realtors might use them to screen people. Job recruiters might use that data to screen people. So it’s very, very damaging to your customers to have that data be leaked into the internet where it could be misused, despite of all that, there’s certainly, there are financial risks, but I think the most important reason to take cybersecurity seriously is out of respect for your customers, creating the trust relationship with your customers that is at the heart of the insurance industry.
Edwin K. Morris (13m 5s):
It is really the root of a lot of different issues. There’s a lot to this. It’s not just a one, check the box we’re done. There’s a lot of parts to this.
Janine Fodor (13m 16s):
There’s a lot of parts to it. And it’s an ongoing issue that is you can’t just do it once. That’s the sad thing. You can’t just fix things up and then not think about it again. You have to keep reassessing. And of course there’s a cat and mouse game that goes on the, the bad guys get more sophisticated. And so the good guys have to get more support.
Edwin K. Morris (13m 37s):
You’ve talked about threat mitigation against things that we know about. What about all the other stuff? We have no idea how this is being used.
Janine Fodor (13m 46s):
Yeah, yeah, no, that’s exactly right. It’s a sort of frightening new world and it’s an evolving world. And, and, but I think just becoming aware and paying attention and, and learning things, I mean,
Edwin K. Morris (13m 59s):
And to stay relevant, you need to stay current.
Janine Fodor (14m 3s):
Absolutely. Absolutely. It’s an obligation we have to our customers into our business.
Edwin K. Morris (14m 8s):
Thank you for bringing all that good information. I’m sure it’ll pull some ostriches out of some sand somewhere and give everybody a heads up.
Janine Fodor (14m 16s):
Thank you. Have a great day.
Edwin K. Morris (14m 19s):
Thanks for listening to this edition of the trusted advisor podcast brought to you by Iroquois group Iroquois, your trusted advisor for all things insurance, and remember get out of the office and sell. This program was recorded live at the Cohen multimedia studio on the grounds of Chautauqua institution. I am Edwin K. Morris, and I invite you to join me for the next edition of the trusted advisor podcast.